but can someone explain the line msgid "" I dont really get how you get a translation for a message without an ID
@Nuxwin Thanks
but can someone explain the line msgid "" I dont really get how you get a translation for a message without an ID
@Nuxwin Thanks
well nuxwin probably cant really check it because according to his sidebar he only can english and french
lemme check this for a sec.
well in General it looks fine, but
line 58 seems empty for the german translation.
welll if the OTP Server has an interface for users uploading their keys or the users are szplied the keys through the company it would be possible but yeah in general it would be a lot less useful.
because you can set up yubiOTP Protocol with your own keys and if you have a setup where you use your keys and dont want to upload them into yubicloud you can make your own server.
this is a problem that U2F doesnt have, because it's an asymmetic concept where no private data has to be exchanged.
Yubikey OTP is a bit of a funny concept:
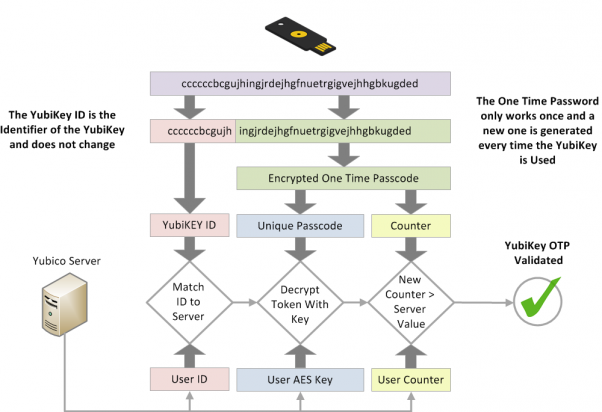
the "Yubico Server" would be in that case whatever server wants to check the OTPs.
Thr Problem is that the "User AES Key" on this graphic is something that can only be obtained by setting up a Yubico OTP with your own keys and then uploading those to the validation server like this https://upload.yubico.com/ (only the AES key as well as the public and private Identity are relevant)
the AES key is essentially used to decrypt the encrypted OTP and in the OTP there is essentially the counter and the Private ID which get checked against what the server knows.
so you can use your own "identity" of a yubikey with your own server but you wont be able to use the identities loaded on the keys by default with your own servers because the keys cant be extracted.
The Yubico OTP protocol itself is open, but it relies on symmetrical keys, and the problem is that you wont have the keys that yubico shipped the yibus with. so you can add a yibico otp config with your own secrets and stuff onto the key but without doing that you dont have the needed data to decrypt the OTP.
pretty similar to the fact that AES is open, but you wont be getting anything decrypted without the key.
well I dunno how the authentication in imscp works under the hood but if you are doing multiple 2FA options, the backup keys should be essentially be a "global" solution (works with any 2FA a user sets up).
Own OTP Servers arent bad, but limited because they cannot really work with the standard YubiOTP which gets shipped but needs to be loaded with custom parameters which have to be agreed upon with the OTP server (that's where symmetrical crypto gets slightly annoying.)
yup that's the "one-time code list" way which imo is splendid (especially if they dont enforce any random order you can take just a part of the list with you so not the entire list gets compromised if something happens)
well.
I have seen 2 approaches;
one-time codes you print out which allow you to get in temporarily (for example if the phone's battery is down in case of TOTP and pther phone-based 2FA) (for example used at Google, protonmail and others)
one code which gets printed out which allows to remove 2FA instantly (I've seen that on steam, Apple, Dropbox and probably others).
I personally prefer the code list because the codes arent re-usable and they dont throw 2FA right into oblivion immediately
but no matter how it's done it essentially is something print out on a piece of paper which can be used if the electronic 2FA cant be used.
that's epic. it imo is a really great thing, totp is the standard because it just works and there's applications in probably any language (I wouldnt be surprised if there's a dos implementation of it) but the security isnt perfect especially considering that pretty much all android devices are vulnerable to an exploit that allows to get root and copy the seeds without leaving a trace, making smartcard-similar security (you could say that U2F is basically a super-constrained cheap smartcard, in a very simplified manner) where those keys cannot be copied makes it great.
but if you do 2FA maybe also add some kind of backup codes that the user can get in in case of problems (e.g. the key broke, got stolen, whatever)
well the not wanting a fallback is not really wrong except maybe if the admin locks himself out because he screwed up the network config with DNS servers that dont work or whatever.
but at least we know that there's no fallback here.
but that's one reason why a 2FA which doesnt have a 3rd party is better in my opinion. because you dont have to rely on that 3rd party

